The Geography of Cyber Warfare
More than 40% of the world's populace now have internet connections, with the number of users slated to reach three billion by the end of this year. If you're reading this, you're one of them.
Over the past year, many of us users have become aware of the extent of cyber snooping and the lack of privacy on the internet. Revelations by WikiLeaks and Edward Snowden, and most recently by Vodafone, starkly describe the pervasive extent of cyber spying.
Some of us have even been the victims of cyber crime, in the form of fraudulent credit card transactions, hacked email accounts, and stolen identities. The internet security company McAffee approximates such crimes to have cost the global economy as much as $575 billion (equivalent to 30% of Canada or India's GDP) just this year alone. Few of us however understand the murkier world of cyber warfare-- a threat to both personal and national security-- that has far more serious implications.
Wikipedia's page on cyber warfare has a fairly detailed description of what forms it can take. The US' decision to identify and charge 5 individuals associated with the Chinese armed forces for a recent slew of cyber attacks, put names and faces to this phenomenon, and caused a diplomatic and trade ruckus. Such attacks can be perpetrated by governments, corporations, groups and even individuals on almost any person, company, institution or government, almost anywhere, and in many forms. Their sole purpose is to stealing information, or cripple their targets, or both. Examples of such attacks include the mysterious appearance of the stuxnet virus that infected and almost shut down Iran's nuclear reactors in 2010. Less well known, is the story of a significant portion of China's internet infrastructure being brought to its knees last year, by carefully coordinated Denial of Service attacks, that snuck past the country's robust security filters and shields.
The motives, targets, origins, timing and magnitude of such attacks are almost impossible to predict, and are usually discovered only after the fact. Given the impact such attacks can have on a government or company's security and credibility, we rarely even get to hear about them.
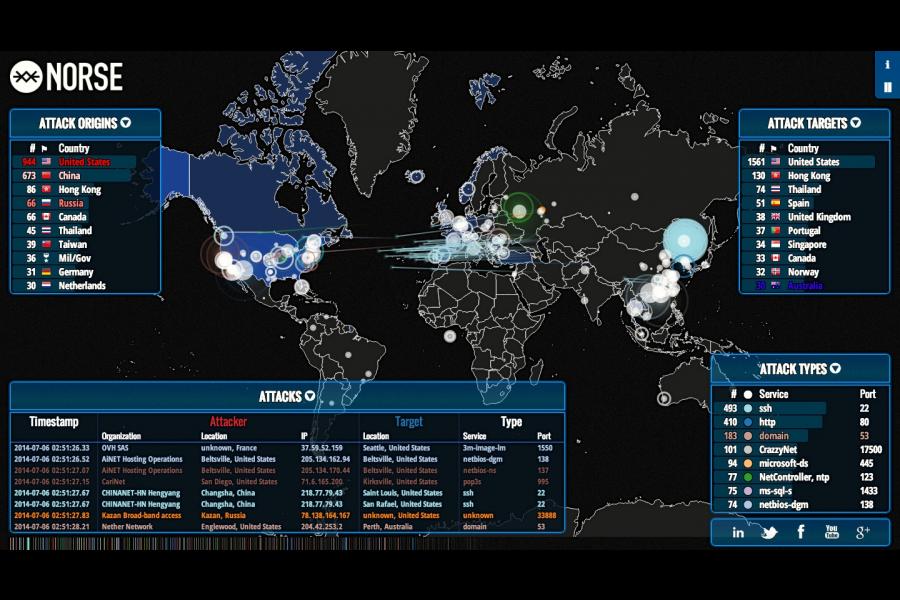
Coming across a fascinating, real-time map of ongoing cyber attacks, finally allowed me to understand the magnitude and geography of the problem, and it isn't pretty. Developed and hosted by internet security company Norse, the map illustrates the hundreds of thousands of such attacks occurring every minute, launched from and at the most unexpected of locations. These patterns and their geographies are the outcomes of new animosities, based on a multiplicity and diversity of interests in a globalized landscape, that only the internet can nurture and sustain.
As I watched the map, I saw tens of thousands of vectors, symbolizing attacks, take off from as many locations across the landmass of Australia and head straight for the west coast of the US. Within seconds, they hit a single point near Seattle, in a giant orange explosion.
Mapping these attacks, makes it obvious that vast resources are already being, and will need to be deployed in the future, to protect not only the targets, but the integrity of the internet itself.
There is opportunity here, but also inherent conflict. The patterns on this map do not follow the conventional geopolitical animosities we see playing out on the ground. They present a new landscape of rapidly shifting allegiances, and battles being fought by anonymous warriors, sometimes within a country's own boundaries.
Addressing this problem will require swifter, more innovative, and far more nimble forms of diplomacy that have yet to be tested. The old men that plod through our corridors of power, aren't going to be able to fight this new war.
Click on the map below, and take a few minutes to watch the battle erupt on your screen. Keep looking at it, and it starts to rival a Diwali or 4th of July fireworks extravaganza.
Though virtual, each vector has the same intent as a missile-- to cripple, if not kill. If this is not war, then what is it?
Note: The map that opens when you click the image below is best viewed on a browser on your laptop or desktop, or an Android OS device. It may not open on an iPhone or iPad.